IDX by authID
The Future of Identity is Here – Reusable, Verifiable, Unphishable
Built on W3C standards, IDX eliminates credential vulnerabilities and delivers secure, reusable identity for a passwordless future.
The Problem
Fragmented identity systems and bolt-on authentication methods fail to protect access across today’s hybrid enterprise. Even worse, external users, contractors, vendors, and partners often operate outside core IAM controls, creating hidden risks.
The result? Escalating threats, growing complexity, and a broken user experience beyond your enterprise perimeter.
Meet IDX:
The Next-Generation Identity Platform
IDX is the future of identity, delivering reusable, verifiable credentials anchored to Decentralized Identifiers (DIDs). Built on the ADIA standard and designed for enterprise scale, IDX brings next-generation authentication to your workforce.
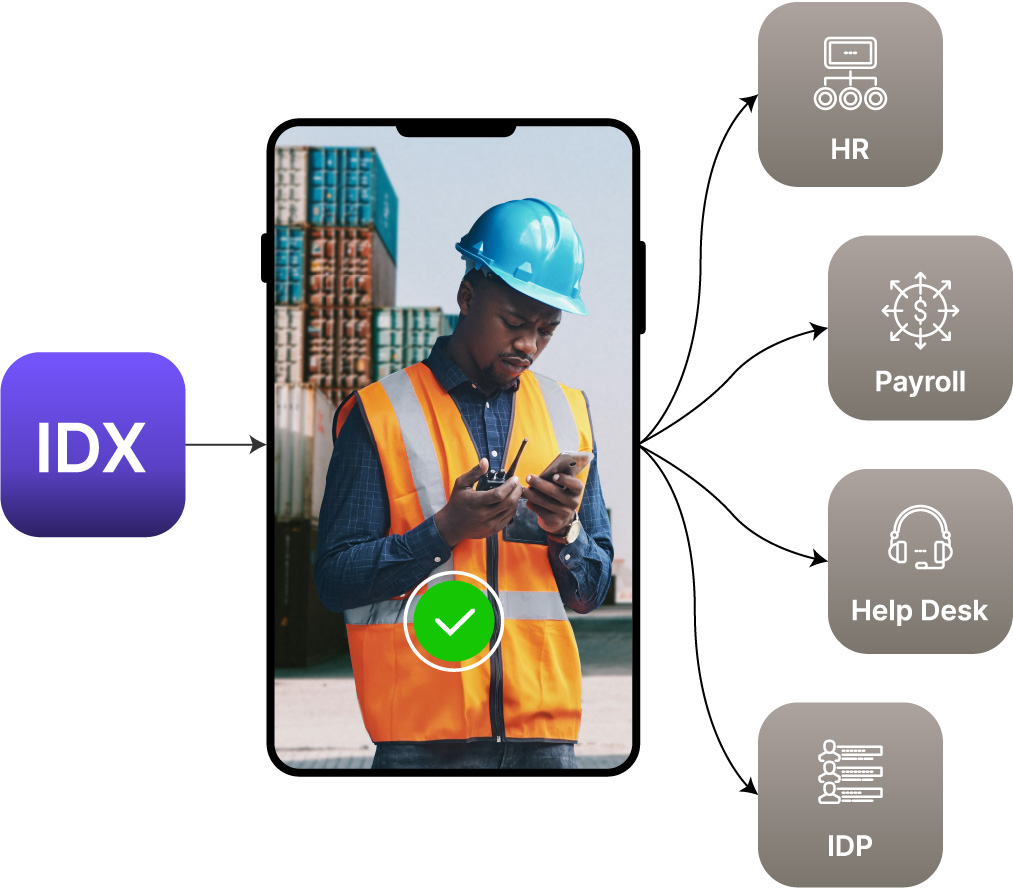
IDX enhances your existing IDP/IGA solution by replacing passwords with phishing-resistant, cryptographically bound biometrics, automating onboarding with integrated identity verification, and enabling seamless credential reuse across systems and organizations.
Future-proof your identity stack with plug-and-play deployment that extends Zero Trust, simplifies lifecycle management, and enforces privacy and compliance.
Key Features
Passwordless, Unphishable Authentication
Best-in-class implementation of PrivacyKey biometrics and FIDO2 credentials ensures every login is phishing-resistant, passwordless, and cryptographically bound to a verified user.
No-Code Deployment & Pre-Built Integrations
Augments your existing IAM stack (Okta, Entra ID, Ping, ForgeRock, LDAP) with no-code configuration and pre-built integrations for tools like Zendesk and ServiceNow; no rip-and-replace required.
Integrated Identity Verification
Built-in Proof™ capability streamlines onboarding with document and biometric verification, enabling users to securely claim their DID and verifiable credentials without manual effort.
Identity Wallet
Give users control of their identity through an iOS and Android wallet.
Verifiable Credentials & DIDs
IDX issues W3C-standard Verifiable Credentials anchored to Decentralized Identifiers (DIDs) enabling tamper-proof, portable, user-controlled identity across systems and organizations.
AI-Driven Lifecycle Automation
Automate onboarding, credential issuance, access updates, and offboarding with policy-based workflows that reduce IT overhead and human error.
Privacy-First Architecture
IDX never stores PII or biometric templates. All verifications are privacy-preserving and fully compliant with global regulations.
Future-Proof Interoperability
Built on the ADIA specification, IDX supports secure, standards-based credential exchange across enterprise boundaries, ready for any trust network, now or next.
How IDX Works
IDX replaces static credentials with high-assurance, reusable identity, handling identity proofing and credential issuance with maximum privacy and precision.
Step-by-Step:
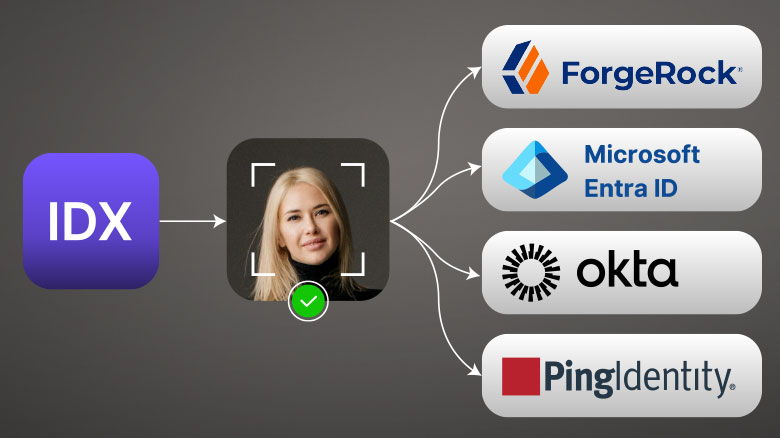
1. Establish Core Identity
Configure IDX to your existing system of record (HR, IAM, LDAP) to establish a Root of Trust.
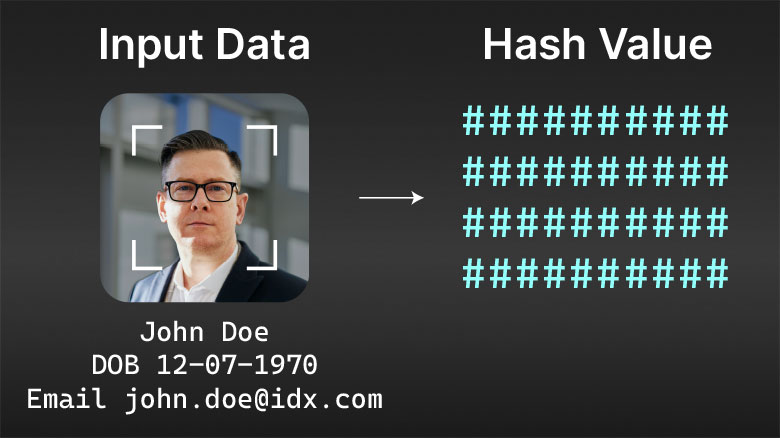
2. Create Identity Blueprint
IDX securely hashes and ingests identity attributes to generate a claimable credential or Decentralized ID (DID).

3. Verify Identity
Users verify their identity using a government issued ID with Proof™ and a biometric authentication secured by PrivacyKey™.

4. Root of Trust Validation
IDX matches the verified identity to system records using cryptographic hashes and, when available, compares biometrics to existing records, preserving privacy while ensuring high-assurance verification.

5. Identity Search & Issue Credential
IDX checks identity hashes and biometrics to detect existing DIDs, issuing a credential to an existing identity or creating a new one to ensure uniqueness.
6. Federation and Reusability
Issued credentials can be reused across systems and organizations – no need to re-verify.
IDX Help Desk Demo
Use Cases
BLANK
BLANK
Enterprise & Workforce Identity Management
Securely manage internal employees, contractors, and vendors using biometric-bound, phishing-resistant credentials.
Supply Chain, Remote Workforce, and Partner Authentication
Provide trusted onboarding and secure, frictionless access across distributed teams, supply chains, and external partners.
Multi-Agency & Cross-Organizational Collaboration
Facilitate secure, interoperable identity federation and credential reuse across agencies and organizations.
Help Desk Agent Authentication
Enhance security by verifying help desk interactions with biometric-backed, high-assurance identity verification.
Consolidation of Siloed Identity Providers (IdPs) and IAM Systems
Unify fragmented identity infrastructures arising from mergers, acquisitions, or departmental silos into one secure, reusable identity across all systems and providers.
Enterprise-Wide Passwordless Digital Transformation
Accelerate secure digital transformation with passwordless, unphishable credentials that eliminate identity attack vectors.
MFA & OTP Replacement
Consolidate identity verification and authentication tools to eliminate vulnerable OTPs and weak MFA methods, significantly reducing costs and closing security gaps.
Smart Cities Infrastructure Access & Management
Enable secure, frictionless, biometric-bound authentication for city workers, vendors, and IoT administrators accessing critical infrastructure and urban systems. Streamline smart city operations, eliminate shared credentials, and ensure auditability across city-wide digital services.
Benefits
Future-Proof Your Identity Infrastructure
Designed to augment, not replace, your existing IAM infrastructure, seamlessly integrating and preparing your organization to adapt to emerging digital identity standards and technologies.
Eliminate Shared & Ghost Accounts
Replace shared credentials with biometric-bound identities, eliminating risk, ensuring accountability, and preventing clerical errors that leave credentials active post-offboarding.
Prevent Credential Phishing & Account Takeovers
Protect your organization with FIDO2 and biometric-backed, phishing-resistant authentication, removing usernames and passwords as a point of compromise.
Seamless Cross-Organizational Identity Reuse
Enable trusted credentials to be interoperable across multiple organizations, dramatically decreasing identity management costs and friction.
Automated User Lifecycle Management
Automate onboarding, offboarding, and provisioning processes, eliminating manual IT tasks and significantly reducing administrative expenses.
Achieve True Zero Trust Security
Extend a consistent, identity-bound security posture across your entire enterprise perimeter—internal and external—by ensuring only verified users gain access, with no reliance on passwords or trusted networks.

IDX Data Sheet
Learn how the IDX Wallet enables secure, portable, and standards-based digital identity management across your workforce

IDX White Paper
Discover how IDX transforms identity management for today’s extended workforce

It’s Official
authID is Among the Leaders in US Biometric Authentication
About authID
authID (Nasdaq: AUID) helps enterprises “Know Who’s Behind the Device™” with a patented biometric identity platform that delivers lightning-fast identity proofing, authentication, and account recovery. Powered by PrivacyKey with no biometric data stored, authID blocks deepfakes, prevents account takeover, and eliminates password risk, enabling the most secure and seamless user experience in the digital ecosystem.

One Enrollment. One Identity. One Biometric. Unlimited Credentials. Set up a demo today!
