For companies competing in today’s borderless and digital world the protection of sensitive systems as well as the confidential data of your customers is critical. When it comes to protecting these assets, the phrase identity as a service (IDaaS) comes up frequently. Significant data breaches and scandals are in the headlines every day, and more companies are beginning to use IDaaS types of service from providers who can help them manage and secure confidential information and sensitive systems using identities.
What exactly is IDaaS? How does it work? What benefits does it offer your business? Here’s a closer look at this service, it’s key components, and a look at the advantages it has to offer.
What is Identity as a Service?
IDaaS Definition: IDaaS stands for “Identity as a service”. IDaaS refers to identity and access management services offered on the cloud or through a subscription, like other SaaS platforms.
The goal of IDaaS is to authenticate users and provide each user with the correct access to files, software, and other resources they’re permitted to use. It also involves collecting intelligence, logging events, and generating reports on users, including when a user accessed a system and what information they accessed for monitoring and audit trail purposes. IDaaS also offers organizations an array of additional benefits, including reduced fraud, enhanced marketing opportunities, and convenient customer services.
Why Is It Important?
Your Customer Data has a direct impact on your bottom line.
Protecting and thoughtfully leveraging digital identity information is critical from both a customer and a business perspective.
Protection begins with recognizing how sensitive customer data is collected, who has access to those records, and how the information is being used.
Companies are held liable when their customer’s data are misused or stolen due to poor maintenance or ineffective data security. This leads not only to business losses but potentially too heavy compliance fines and other legal penalties for data mismanagement.
“78 percent of businesses are driven by the need to meet industry best practices for security preparedness. All companies considering biometrics indicate that user experience is the main factor involved.”
Who uses Identity as a Service (IDaaS)?
Any business that needs to verify the identity of a person online, on the phone, or in a physical
location, will benefit from using IDaaS. There are a variety of use cases that IDaaS supports such as access to digital proprietary information or even physical access to their secure rooms in buildings.
Top IDaaS Industries
- Lenders and Financial Institutions.
- Gig-Economy.
- Education, Government, and Religious Institutions.
- Managed IT Service Providers.
- Logistics, Healthcare, and Warehousing.
- Security Companies.
The Benefits of IDaaS
Using identity as a service offers several significant benefits to businesses, principally cost savings, access to industry-leading expertise, and efficiency. Dealing with identity at an enterprise level using the software can be costly – it requires your team to maintain a data center or pay hosting fees, to provision and maintain servers, to purchase, install, and upgrade software, data backup, and above all to have an IT team which is focused on identity management to maintain this platform at the highest level.
IDaaS providers have the resources, facilities, and expertise to provide state-of-the-art solutions that meet your needs. Their costs are amortized across all the customers that use their services, which enables them to invest in all the latest technology and to constantly innovate. The bad actors are constantly finding ways to hack your systems and it is essential that the protective technologies employed by the IDaaS providers are constantly updated. As a company, you have the benefit of that expertise and investment without having to engage in it or even understand it yourself.
With an IDaaS provider, you’ll enjoy added security and efficiency with significant savings in time, with fewer password resets and more trusted logins by your users. No matter where a user is logging in from, the process will be secure and seamless. The additional security offered with this solution can also keep your business from dealing with a breach or hack that could be devastating enough to harm your reputation and even destroy your business.
Moving identity to the cloud, just like you may have done with email systems or network security monitoring, improves efficiency, offers significant savings, and gives you expertise from proven vendors. Identity as a service continues to evolve and grow, and it’s offering companies a way to improve user experience and boost security in a cost-effective way so they can grow their business with less worry.
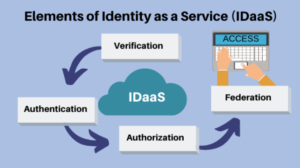
Core Aspects of IDaaS
A variety of features and functionality are provided by IDaaS solutions depending on the market segment and vendor you choose. Some of the common functions and components of identity as a service include:
- Password Management and Authentication – IDaaS services incorporate a variety of means of password management and authentication, an essential requirement of access and identity management. This may include features like multi-factor user authentication via biometrics, passwords, or digital access cards maintained across a variety of access points and devices.
- Multi-tenant, Cloud-Based Architecture– The IDaaS vendor should operate a cloud-based platform that services multiple customer organizations to provide this service, allowing the vendor to issue system fixes, performance improvements, new features, and updates to customers in real-time.
- Analytics and Intelligence – With advanced identity services, analytics, and intelligence capabilities can provide reports on the use of access privileges among users, as well as information on application, responsibilities, data usage, and more.
- Compliance, Risk, and Governance – By leveraging the intelligence and automation capabilities of these systems, businesses can better manage compliance, risk, and governance.
Single Sign-On in the Network Perimeter
One of the notable applications for IDaaS is single sign-on. This application allows users to only sign in one time within the network perimeter. With that one effort, they can obtain access to the parts of the company’s resources and programs they’ve been authorized to use. It’s fast, easy, and secure, keeping users from the need to continually sign into different programs or resources within the network.
Multi-Factor Authentication to Verify User Identity
It’s important to understand multi-factor authentication since it’s a core component of IDaaS. This form of authentication has become increasingly deployed and in some industry, segments mandated as a method of verifying the identity of users. As the name suggests, multiple pieces of identifying information are required before access is granted. For example, a user may need to provide a password, have a device, and confirm a code. In most cases, two or more of these criteria are used for multi-factor authentication:
- Knowledge – This is something that the user knows, like a password
- Possession – Something that a user has, such as a laptop or a smartphone
- Inheritance – Something that’s a part of the user, such as a retina scan, fingerprint, or facial print.
Multi-factor authentication provides additional security, reducing the risk of unauthorized access. It is generally recognized that the traditional user name and password combination no longer provide adequate protection in light of the massive data breaches which have exposed billions of users’ log-in credentials and many people’s inability to maintain hundreds of unique, strong passwords. Therefore, it is broadly recognized that something more is required to protect sensitive data and systems and to restore trust in those systems. Multi-factor authentication, especially those methods using biometrics may provide the solution.
Biometrics as a Part of IDaaS
The inheritance criteria or biometrics will soon be more frequently deployed as a part of the multi-factor authentication process. Fingerprints are a common form of biometrics used within IDaaS systems, but some vendors are beginning to turn to other forms of biometrics as well, such as facial recognition, handprints, retina recognition, thumbprints, and DNA. With today’s digital and mobile transformation, it is important that the IDaaS provider offers a biometric solution that can be easily and cost-effectively mobilized to the smartphones broadly deployed. When used with other forms of verification, such as a password, adding biometrics to the authentication process can provide another layer of security to keep your company’s information safe.
Top 10 IDaaS providers of 2019
- authID
- Aware
- Jumio
- Experian
- TrustID
- Okta
- Centrify
- One Login
- Ping Identity
- Microsoft
What should you look for in an IDaaS provider?
- Identity proofing with live biometrics
- FIDO2 Passwordless Authentication
- Strong Multi-Factor Authentication with High assurance levels in real-time
- Frictionless
- Scalability
- Adaptability
The improved security will keep your company from facing a hack or breach that could ruin your business. Remember that you are the steward of your customers’ data and it will benefit your business to secure and maintain those accounts.