What is Unphishable Multi-Factor Authentication?
By Brittney Liburd, Senior Product Manager, authID.
Unphishable MultiFactor Authentication (MFA) is the new mandate for multifactor authentication. It is authentication that functions without the use of phishable factors like push notifications or SMS.
The Federal Government Mandates Unphishable MFA
On January 26, 2022, the White House issued a clarification memo for Executive Order 14028 that focused on improving the nation’s cybersecurity posture and ordered federal government agencies to advance toward zero trust architecture. The memo’s gave timelines and demanded concrete deliverables from federal entities. As a result, any organization seeking to do business with the federal government was also instructed to secure its supply chain to further strengthen security across the organizations that service or “touch” government data.
“For routine self-service access by agency staff, contractors, and partners, agency systems must discontinue support for authentication methods that fail to resist phishing, such as protocols that register phone numbers for SMS or voice calls, supply one-time codes, or receive push notifications.” – “Moving the U.S. Government Towards Zero Trust Cybersecurity Principles.” – EO 14028 clarifying memorandum
For the first time, the federal government told its agencies, organizations that serve them, and the rest of the world to stop using MFA solutions that cannot resist phishing. Yet the world’s most popular authentication solutions – even those that are passwordless – still employ phishable factors such as push notifications, PINs, and OTP. With data breaches rising, this guidance will inevitably spill over to private sector organizations as they march towards zero trust architectures to safeguard their businesses, people, and resources.
In this post, we will define unphishable MFA, explain its importance, and show you how to determine if your MFA is unphishable.
What is Unphishable MFA?
Unphishable MFA is multifactor authentication that uses unphishable factors to authenticate. Unphishable MFA protects against unauthorized access and data breaches better than legacy MFA because it removes factors and workflow that could aid in a successful breach or attack. Factors like SMS and push notifications can be hijacked, stolen, or otherwise leveraged for attack and therefore have been deemed unusable by the U.S. government and should be avoided as known vulnerabilities.
Figure 1 – Can You Phish It?
| PHISHABLE FACTORS | UNPHISHABLE FACTORS |
| Passwords | Biometrics |
| Push Notifications | SmartCards & Hardware Security Keys |
| SMS | Cryptographic Security Keys |
| One-time Passwords (OTP) | |
| Token-based OTPs | |
| Knowledge-based Authentication (KBA) | |
| Magic Links | |
Unphishable vs Phishing Resistant MFA – What’s the difference?
“Unphishable” and “phishing resistant” are terms that security professionals are beginning to use interchangeably. However, many authentication methods leveraging phishable factors are considered phishing resistant by the market. The most well-known are device-dependent options that use push notifications. These options are vulnerable to push-bombing attacks; social engineering attacks that should realistically fail the phishing resistance test. By understanding this differentiation in authentication solutions, cybersecurity professionals began to distinguish solutions that meet the “phishing resistant MFA” market standard from those that use no phishable factors-defining the latter as truly “unphishable MFA”.
What Does Unphishable MFA Mean For Cybersecurity Professionals?
As credential stuffing, social engineering, business email compromise and various forms of credential-based attacks continue to be the leading vectors for unauthorized access, data exfiltration, and ransomware, cybersecurity professionals need to adopt strategies that put identity at the center. According to a recent Gartner report, “The legacy approach to IAM fails to address security risk pervasively or in real-time — nor does it align with zero trust strategies.”
“The legacy approach to IAM fails to address security risk pervasively or in real-time — nor does it align with zero trust strategies.” – Gartner, Identity-First Security Maximizes Cybersecurity Effectiveness
In addition, cybersecurity professionals that work with the government in any way will have to begin evaluating the solutions they have chosen for MFA to see if they are unphishable- this will inevitably spill into the private sector and eventually into CIAM.
Why is Unphishable MFA Important?
Today’s legacy MFA relies heavily on validating what the user possesses and entirely omits validating the user’s identity. We have seen that failure to properly identify the user behind the device allows threat actors to gain access to the network and masquerade as legitimate users through lateral movement. In some cases, we have seen these actors go as far as to enroll their own MFA authenticators into legitimate user accounts.
Distributed workforces present modern challenges in authentication as the network perimeter has evolved to the “user perimeter” – where every user and their devices are an opportunity for compromise. While legacy MFA is better than nothing at all, it’s time to move to MFA which accounts for these shifts in the workforce and the human factor in authentication, helping to protect users from today’s prevailing cyber-attacks.
In a nutshell, unphishable MFA is important because:
- Most Popular solutions for MFA cannot defend against social engineering, prompt-bombing, and phishing.
- The Market needs unphishable MFA to meet federal directives.
- Unphishable MFA is the next logical step in mass migration to Zero Trust Architectures. The never trust, always verify thought process of Zero Trust is actually at odds with legacy MFA as it trusts that the user is always the person in control of both the device attesting for identity and the device being used for access.
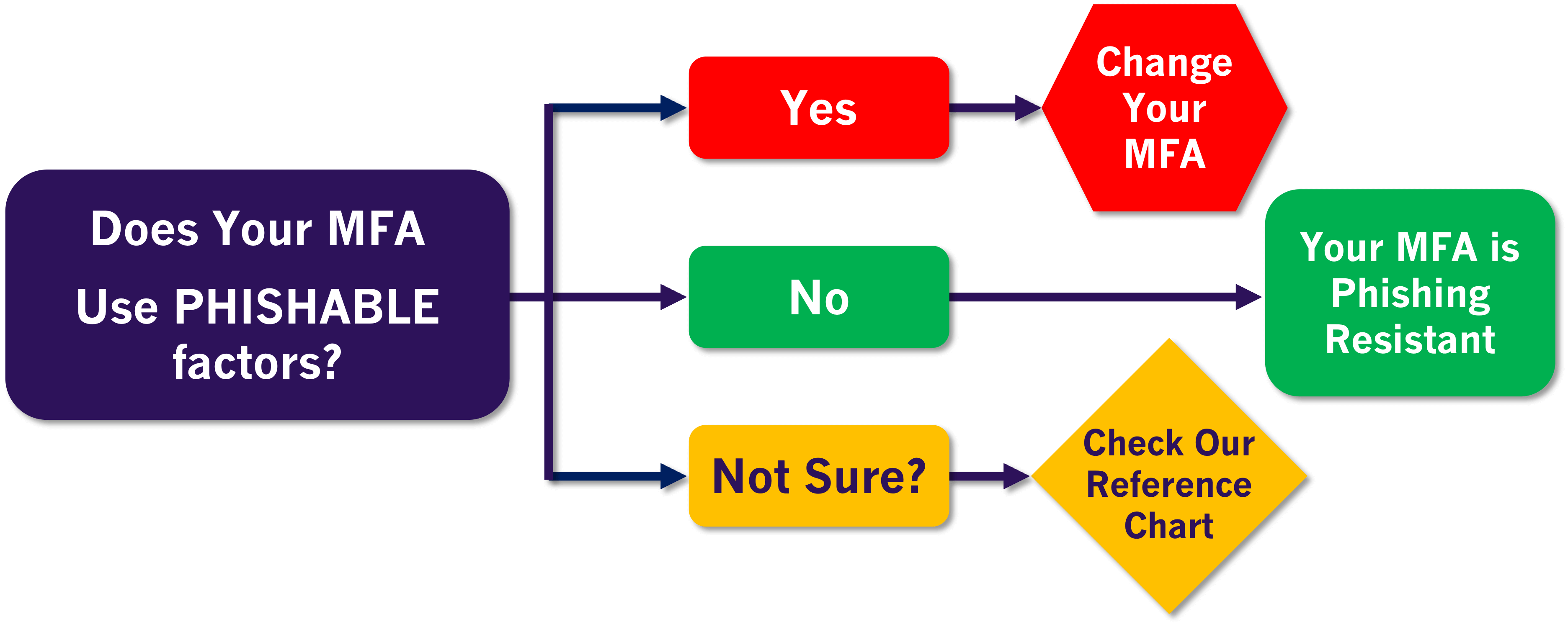
How to Tell if Your MFA is Unphishable
Figuring out if your MFA is Unphishable is pretty simple. For convenience, we have reprinted figure 1 from above side-by-side with an easy-to-follow flowchart.
| PHISHABLE FACTORS | UNPHISHABLE FACTORS | |
| Passwords | Biometrics | |
| Push Notifications | SmartCards & Hardware Security Keys | |
| SMS | Cryptographic Security Keys | |
| One-time Passwords (OTP) | ||
| Token-based OTPs | ||
| Magic Links | ||
| Knowledge-based Authentication (KBA) | ||
If your MFA doesn’t use any phishable factors, it is unphishable MFA.
Verified is Unphishable MFA
Human Factor Authentication, or HFA, is a hybrid approach to MFA that truly combines what the user has with who the user is, the proven way to combat the prevalent threats facing organizations today. Device possession is proven using FIDO2 (Fast Identity Online), an open standard that combines a cryptographic key stored on the device and device-based biometric/pin; user identity is verified using a cloud selfie that has been bound to the user’s identity. Combined, these two factors always provide high assurance of the user’s identity, moving organizations further down the path to their Zero Trust journey in a more efficient manner than rip-and-replace.
Why use Verified Unphishable MFA?
Verified users cannot be prompt bombed. Push notifications are vulnerable to prompt-bombing attacks and are responsible for successful breaches that would not have been possible with Verified. Verified does not use phishable factors, including credential/password pairs or one-time passwords so there’s nothing to steal. Additionally – the process of taking a selfie is a little more involved than slapping your phone at 2 am to make the notifications stop.
Verified cannot be hijacked. In March 2022 the “Scatter Swine” attackers sent text phishing messages to trick employees into giving over their credentials. The attackers used an auto-forward feature on Telegram to simultaneously send the entered credentials to the attackers and submit them to the site the victim was trying to access. Verified authenticates users on the primary device, or device they are using for access – there is never a need for credentials or passcodes that can be stolen.
Verified is more flexible than WebAuthn. Though WebAuthn has many advantages over legacy MFA – the standard has a number of shortcomings. For example- WebAuthn is not compatible with older or less popular browsers like Internet Explorer or Linux, can’t integrate with CIAM platforms, and has limited developer support. In addition – WebAuthn’s recovery process is the stuff of nightmares. Verified has none of these issues – we work across browsers and devices seamlessly, integrate elegantly with existing solutions, and offer full support and deep developer documentation.
We don’t make users hate us. MFA adoption is known to struggle due to the user experience. The requirement of a second device in order to complete verification and the cumbersome recovery process if they forget their password or their device is stolen adds unnecessary friction for users. Verified can enroll, recover, and authenticate on the device being used for access and requires no such additional steps.
Verified is Unphishable MFA. Maximize your cybersecurity’s effectiveness with user-centric, biometrically-backed authentication from authID.
To learn more, schedule a time with our security specialists.

